Tool Kits -- CIO CTO Tools
IT Job Descriptions
IT Infrastructure
Security - Disaster Planning
 Tool Kits -- CIO CTO Tools - IT-ToolKits.com is the resource site forInformation Technology management. This site contains the Information Technology and management infrastructure tools that the CIO, CSO, and CFO can use for Sarbanes Oxley, Disaster Recovery, Security, JobDescriptions, IT Service Management, Change Control, Help Desk, Service Requests, SLAs - Service Level Agreements, and Metrics. Site includes Browser and Operating System Market Share White Paper and IT Salary Survey Data. Tool Kits -- CIO CTO Tools - IT-ToolKits.com is the resource site forInformation Technology management. This site contains the Information Technology and management infrastructure tools that the CIO, CSO, and CFO can use for Sarbanes Oxley, Disaster Recovery, Security, JobDescriptions, IT Service Management, Change Control, Help Desk, Service Requests, SLAs - Service Level Agreements, and Metrics. Site includes Browser and Operating System Market Share White Paper and IT Salary Survey Data.
2023 Edition of IT Management Tool Kit Released 
CIOs and CTOs are in a constantly evolving field, however world class CIOs and CTOs focus on three areas to help them manage more effectively. They are:
- Technology
- People
- Infrastructure
Over 2,400 pages of "Best Practices", tips and techniques, policies, procedures, job descriptions, electronic forms and much more. Ready for immediate download.
IT Management Tool Kit Read on Order
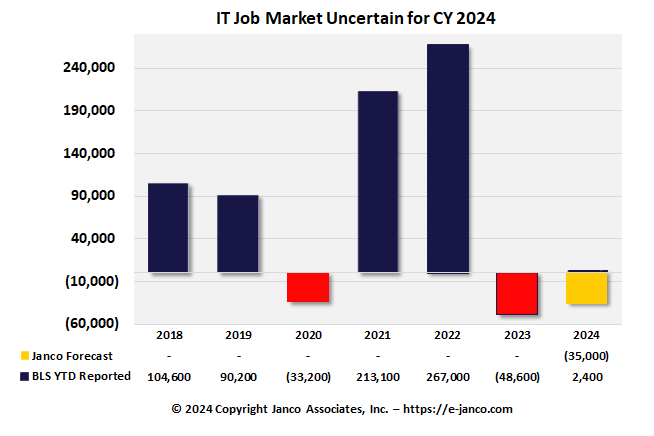
IT Job Market Loses
The IT job Market is showing IT hiring slows with reduction in the size of the IT Job Market
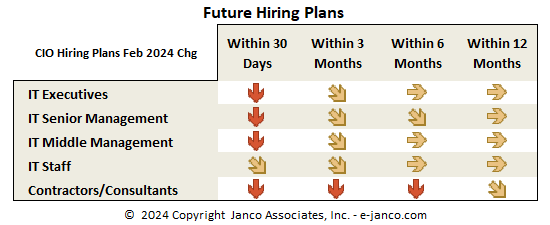
Hiring Plans
For more go to IT Job Market News.
|
IT Toolkits focus
IT-Toolkits.com supports a wide range of industries and enterprises of all sizes. Our clients include over 2,500 premier corporations from around the world, including over 250 of the Fortune 500.
IT Salary Survey
NEWS -- The IT Salary Survey is now available. Study shows that IT salaries have fallen. Companies that participate get a free copy of the next survey when it is released. 
Read On IT Salary Survey..

Read on...
Site Map
Special Offers
IT Service Management
CIO Productivity Bundle
IT Hiring Resource Kit
SOX Compliance Resource Kit
DRP & Security Bundle
Job Description Bundles
|


Over 324 updated IT job descriptions
Read On...

Between hackers, natural disasters, or even a pipe breaking in the office above yours, every enterprise needs a business continuity plan. It often is the difference between riding out a problem and going out of business. For this reason, most enterprises focus on the safety of their backup. Data loss is significant concern for everyone - and has huge financial consequences. Solutions typically require multiple processes and procedures.
Read on DR/BC...
|










